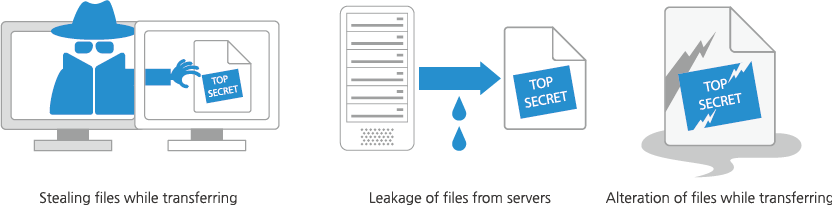
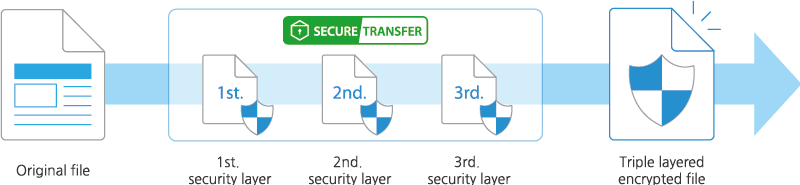
Exacoola
Device to devicefile transfers
Exabyter
Improve websitefile transfers
Albert
Vision AI forsmart traffic
Costomi
IP cameracloud factory

Workstation
Transfer large files between macOS at high-speeds and automate the repetitive file transfers

Workstation
Transfer large files between macOS and Windows at high-speeds, and automate the transfers

Workstation
Transfer large files between long-distance H.Q. and branch Windows, and automate the transfers

Cloud devices
Transfer large files directly between AWS S3 in different regions, and automate the transfers

Cloud devices
Transfer large files directly between AWS S3 and MS Azure blob storage, and automate the transfers

Cloud devices
Transfer large files directly between Google storage and MS Azure blob storage, and automate it

Collection
Automate large file collection from 100 x Ubuntu Linux to AWS S3

Collection
Automate large file collection from 10 x Windows to CentOS Linux

Distribution
Automate large file distribution from Windows to 50 x Redhat Linux
Partners
Software Product Vendor
Integrate Exacoola, Exabyter's file transfer capabilities into your products and services.SI, Development, IT Solution Provider
Create new business opportunities with Exacoola, Exabyter file transfer products.IP camera supplier
Distribute IP camera products with your brand logo or produce them locally.Transportation system provider
Unlock new opportunities in government business with new smart traffic AI products.Products
Exacoola
Device to device file transfers
Automatic file transfer
from macOS to macOS

Automatic file transfer
from Windows to macOS

Automatic file transfer
between H.Q. Windows
and branch Windows

Automatic file transfer
between AWS S3
in different regions

Automatic file transfer
from AWS S3
to MS Azure blob storage

Automatic file transfer
from Google storage
to MS Azure blob storage

Automatic file collection
from 100 Ubuntu devices
to AWS S3

Automatic file collection
from 10 Windows devices
to CentOS

Automate large file distribution from Windows to 50 x Redhat Linux
Exabyter
Improve website file transfers
Upload and download large files of 1TB or more on web service
Enables users to transfer large files in the fastest and most seamless way possible on web service.
Upload and download 10,000 files or more on web service
Enables the fastest and most seamless transfer of millions of files and folders across web services.
Upload and download files with the folder structure intact on web service
Provides the fastest and most reliable file transfer across large-scale web services.
Upload and download files with the folder structure intact on web service
Provides the fastest and most reliable file transfer across large-scale web services.Albert
Vision AI for smart trafficLanguage
- English
- 한국어
- Tiếng Việt
Partners
Software Product Vendor
Integrate Exacoola, Exabyter's file transfer capabilities into your products and services.SI, Development, IT Solution Provider
Create new business opportunities with Exacoola, Exabyter file transfer products.IP camera supplier
Distribute IP camera products with your brand logo or produce them locally.Transportation system provider
Unlock new opportunities in government business with new smart traffic AI products.